Smarter AP,
thanks to AI.
Medius AP management software replaces the work and worry of invoices with AI and automation, so you can wrap up and rest easy.
NEW Now available: Season 2 of our award-winning podcast, Accounts Deceivable. Listen now

Medius AP management software replaces the work and worry of invoices with AI and automation, so you can wrap up and rest easy.
Medius goes beyond automation to make AP autonomous. With intelligent technology to capture, process, and pay your invoices, our AI keeps learning and improving, getting smarter (and making your life easier) with every invoice.
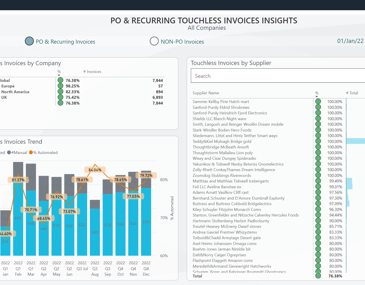
Streamline accounts payable and boost cash flow visibility.
Simplify AP by getting rid of paper and eliminating manual tasks like keying, matching, and processing invoices. Get full visibility into invoices, spend, and cash flow, so you can close the books on time, every time.
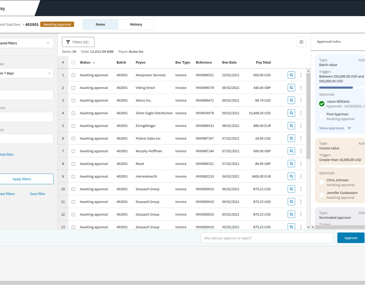
Simplify supplier payments to save time and money.
Remove complexity, reduce fraud, and save money by improving your payments process. Medius Pay overhauls the way you pay suppliers, removing manual chores (like processing checks) with automated work.
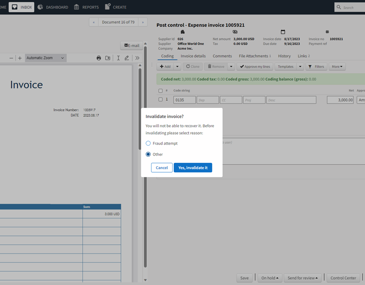
De-risk your spend and gain visibility and control across the invoice to pay lifecycle.
Relax and let machine learning and AI ensure your policies are enforced. Gain visibility into your fraud and risk exposure with new insights with a solution that integrates with the Medius suite.
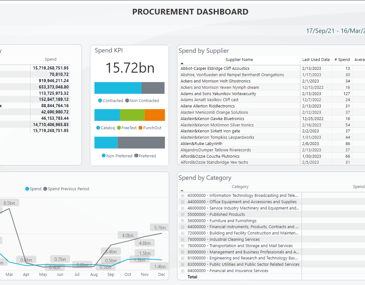
Take control of your spending.
Put an end to maverick spend. Give buyers the means to intimately understand suppliers, automate tedious tasks, set up approval chains, and more.
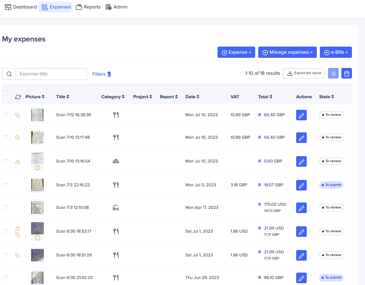
Automate and control business expenses without complexity and heartache for your employees.
With expense management solutions from Expensya, now part of Medius, you get control of business expenses without adding complexity. Using intelligent technologies like AI and ML, expense reports are automatically populated with itemized, categorized charges. Employees don’t have the hassles of filling out expense reports, or chasing paper receipts and you get visibility into what you’re spending and where you can save.
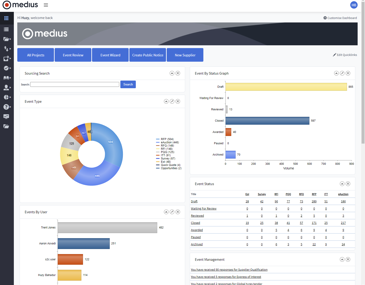
Get the right suppliers for the best price.
Medius software lets you run comprehensive sourcing events with maximum visibility, so you can see deeper into identification and negotiation. There’s no better way to find better suppliers.
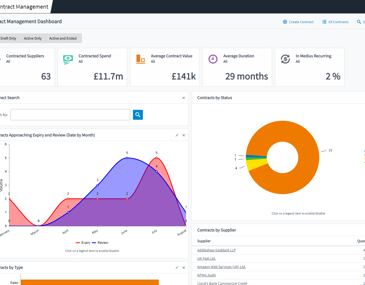
See and control supplier agreements.
Rescue your procurement team from paper purgatory with Medius Contract Management. You’ll get complete control over your supplier agreements in one simple system, so you never miss a renewal.
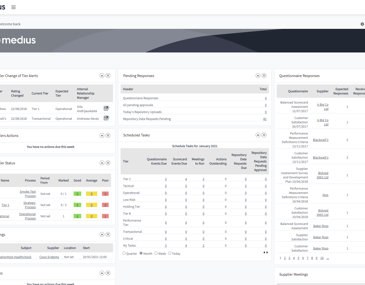
Reduce supplier risk and boost performance.
Medius Supplier Onboarding is one package that maintains accurate vendor data, so you save precious time and money. It also improves vendor relationships with ongoing performance measurement and collaboration tools.
Automate the entire source-to-pay process with the Medius Accounts Payable suite, because there’s no better time to do AP better.
Listen in to season 2, as we continue to look at the real-life, human impact of invoice fraud: a fast-rising, white-collar crime with compounding ripple effects beyond just money lost. We hear true stories from victims and perpetrators of fraud and go deeper into what drives someone to corruption and crime.
There's no better time to do AP better.
Join the accounts payable revolution and unleash your business's true potential. Watch the video and see what Medius can help you achieve.
Spend a few minutes exploring our interactive demo, and save your AP team months of manual work! Click below to experience our solution first hand.
This in-depth, 13-minute video, led by one of our product experts, will show our solutions in action and how they can transform your AP.
Find out how much you can save with Medius AP Automation
Enter a few simple numbers (this might be the last time you have to key things in!) to see how much you can save with Medius. Our tool lets you compare your metrics with those of Medius customers. Download a custom savings report to build your business case.
"Before, it felt like we were missing something, but Medius gives us peace of mind. We feel confident that we’re handling all invoices in a timely manner."
Jason Mayfield
Director of Accounting, NIC Global

Improve your AP process, get more control and compliance and understand your cashflow without adding to your to-do’s. We have a team of subject matter experts that can help you with process improvements, new feature support and more.
